- Tshark can be used to capture and analyze traffic. It offers more functionality than the standard tcpdump and may become your go-to tool to grab the right packets from the network. See the full article at: Tshark: 7 Tips on Wireshark's Command-Line Packet Capture Tool.
- Tshark – Command Line If you haven't had a play with tshark, this program is often overlooked but is a great way to capture application layer sessions on a remote system. The advantage over tcpdump is you can capture and view application layer sessions on the fly, as the protocol decoders included in Wireshark are also available to tshark.
- Wireshark Cheat Sheet Sans
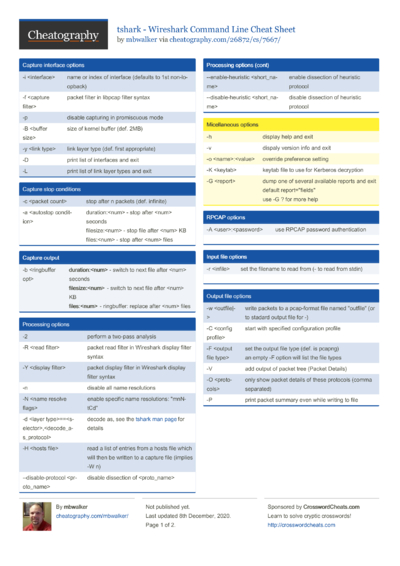
- Tshark Cheat Sheet
- Tshark Tutorial
- Tshark Cheat Sheet Download
- Tshark Cheat Sheet
Manual Pages
The following man pagesare part of the Wireshark distribution. They are available via theman command onUNIX® /POSIX®systems and HTML files via the 'Start' menu on Windows systems.
Wireshark Cheat Sheet Sans
Home Instant Answers Tshark Cheat Sheet Next Steps. This is the home page for your Instant Answer and can be.
androiddump - Provide interfaces to capture from Android devices
capinfos - Prints information about capture files
captype - Prints the types of capture files
ciscodump - Provide interfaces to capture from a remote Cisco router through SSH.
dftest - Shows display filter byte-code, for debugging dfilter routines.
dumpcap - Dump network traffic
editcap - Edit and/or translate the format of capture files

extcap - The extcap interface
idl2wrs - CORBA IDL to Wireshark Plugin Generator
mergecap - Merges two or more capture files into one
mmdbresolve - Read IPv4 and IPv6 addresses and print their IP geolocation information.
randpkt - Random packet generator
randpktdump - Provide an interface to generate random captures using randpkt
rawshark - Dump and analyze raw pcap data
reordercap - Reorder input file by timestamp into output file
sshdump - Provide interfaces to capture from a remote host through SSH using a remote capture binary.
text2pcap - Generate a capture file from an ASCII hexdump of packets
tshark - Dump and analyze network traffic
udpdump - Provide an UDP receiver that gets packets from network devices (like Aruba routers) and exports them in PCAP format.
wireshark-filter - Wireshark display filter syntax and reference
wireshark - Interactively dump and analyze network traffic
Capture filtering is handled by libpcap, and its documentation is part of the libpcap distribution.
I have a lot of traffic...

ANSWER: SteelCentral™ AppResponse 11
- • Full stack analysis – from packets to pages
- • Rich performance metrics & pre-defined insights for fast problem identification/resolution
- • Modular, flexible solution for deeply-analyzing network & application performance
Editcap split pcap
Splitting pcap files in wireshark, Up vote 21 Down vote. Use the editcap utility which is distributed with Wireshark. I found a great tool for splitting pcap files: PcapSplitter. It's part of the Editcap is a program that reads some or all of the captured packets from the infile, optionally converts them in various ways and writes the resulting packets to the capture outfile (or outfiles). By default, it reads all packets from the infile and writes them to the outfile in pcap file format.
how to split a pcap file into a set of smaller ones, Splitting a big capture file. If you have a big file you can quite easily split it into smaller files,using editcap. editcap is a command line tool that is I know this answer is a little late, but it may serve other people as well. I found a great tool for splitting pcap files: PcapSplitter.It's part of the PcapPlusPlus library which means it's cross-platform (Win32, Linux and Mac OS), and it can split pcap files based on different criteria such as file size (what you seem to need) but also by connection, client/server IP, server port (similar to
PCAP Split and Merge | Packet-Foo, Editcap is a program that reads some or all of the captured packets from the infile, optionally Editcap is able to detect, read and write the same capture files that are pcap(3), wireshark(1), tshark(1), mergecap(1), dumpcap(1), capinfos(1), If you have a big file you can quite easily split it into smaller files,using editcap. editcap is a command line tool that is installed together with Wireshark. This is why it is a good idea to add the Wireshark installation path to your path variable so that you can run the command line tools everywhere.
Tshark

tshark, TShark is a network protocol analyzer. It lets you capture packet data from a live network, or read packets from a previously saved capture file, either printing a Installation is a gateway drug. Different systems will report different interfaces. tshark will treat the first interface as the default interface and capture from it by default.
D.2. tshark: Terminal-based Wireshark, TShark is a terminal oriented version of Wireshark designed for capturing and displaying packets when an interactive user interface isn't necessary or available. Wireshark is the world's foremost and widely-used network protocol analyzer. It lets you see what's happening on your network at a microscopic level and is the de facto (and often de jure) standard across many commercial and non-profit enterprises, government agencies, and educational institutions.
tshark(1): Dump/analyze network traffic, TShark is a network protocol analyzer. It lets you capture packet data from a live network, or read packets from a previously saved capture file, either Tshark.dev. tshark.dev is your complete guide to working with packet captures on the command-line. The focus is on doing everything in the CLI because that is an interface your scripts and programs can use. Bash features prominently here, with some examples also in python and ruby.
Tcpdump cheat sheet
tcpdump Cheat Sheet - Complete With Full Examples, The tcpdump cheat sheet covers: Installation commands; Packet capturing options; Logical operators; Display/Output options; Protocols; Common tcpdump Cheat Sheet A commonly used and priceless piece of software, tpcdump is a packet analyzer that packs a lot of punch for a free tool. We put together a list of essential commands and put them in the tcpdump cheat sheet to help you get the most out of it.
[PDF] tcpdump, Command Line Options. -A. Print frame payload in ASCII. -c Exit after capturing count packets. -D. List available interfaces. -e. Print link-level headers. tcpdump Cheat Sheet Installation Commands CENT OS and REDHAT $ sudo yum install tcpdump Fedora $ dnf install tcpdump Ubuntu, Debian and Linux Mint #apt-get install tcpdump
TCPDUMP: a simple cheatsheet, tcpdumpruns under the command line and allows the user to display TCP/IP and other packets being transmitted or received over a network to tcpdump usage tcpdump [-aAenStvxX] [-F filterfile] [-i int] [-c n] [-r pcapfile] [-s snaplen] [-w pcapfile] [‘bpf filter'] -A display payload -c n display first n packets-D list interfaces -e display data link header -F read filter expression from file -i listen on specified interface -n do not resolve IP addresses / ports
Tcpdump count packets
tcpdump, I wouldn't use tcpdump (or tshark ) for this. Instead I'd use iptables to count the packets over a period of time # Prepare two sets of counters and -c count Exit after receiving count packets. --count Print only on stderr the packet count when reading capture file(s) instead of parsing/printing the packets. If a filter is specified on the command line, tcpdump counts only packets that were matched by the filter expression. -C file_size
Man page of TCPDUMP, There is, in fact, no packet count in the file header (because the format was designed to be writable in tcpdump -r test.cap 2>/dev/null| wc -l. Packets 'received by filter.' The meaning of this depends on the OS on which you're running tcpdump, and possibly on the way the OS was configured.If a filter was specified on the command line, on some OSs it counts packets regardless of whether they were matched by the filter expression, and on others it counts only packets that were matched by the filter expression and were processed by tcpdump.
Tcpdump - counting outgoing and incoming UDP packets, Know your network with this powerful packet capture tool. Another tip is to use count -c on the remote tcpdump to allow the capture to finish I am interested in getting a count of all LDAP/Kerberos/DNS packets. I tried the following, but this captures the full packet. tcpdump -i any -Z root 'tcp port 389 or tcp port 88 or udp port 53' -w ~/ldap_kerberos_dns.cap . Is there a way I can just capture how many ldap/Kerberos/DNS packets were exchanged without actually capturing the full
Tcpdump gzip
Write tcpdump output to compressed / gziped file, avoid trying to run tcpdump if gzip obviously failed to start { [ -n '$gzip_pid' ] && [ '$gzip_pid' -gt 0 ] && kill -0 '$gzip_pid'; } || exit 1 tcpdump For example, specifying -z gzip or -z bzip2 will compress each savefile using gzip or bzip2. Note that tcpdump will run the command in parallel to the capture, using the lowest priority so that this doesn't disturb the capture process.
Man page of TCPDUMP, tcpdump -w - | ( gzip -c > output.pcap.gz & ). The other is to just have the files written out in their normal format, and then use a post-processing For this I start using following tcpdump command and capture them to a file: tcpdump -n -i eth0 dst port 53 >> dns_data.log But the file size is high when I run this for long time. How can I capture this to a compress file? I tried below command but its not working. tcpdump -n -i eth0 dst port 53 | bzip2 -c >> dns_data.bz2
I/O Efficient GZip Compression of Packet Captures, tcpdump -i eth0 -w - | ssh forge.remotehost.com -c arcfour,blowfish-cbc -C -p 50005 'cat - | gzip > /tmp/eth0.pcap.gz' - (TCPDUMP & Save -----Original Message----- From: owner-tcpdump-workers sandelman ottawa on ca [mailto:owner-tcpdump-workers sandelman ottawa on ca]On Behalf Of Rob Braun Sent: Wednesday, February 26, 2003 02:16 To: Guy Harris Cc: tcpdump-workers tcpdump org Subject: Re: [tcpdump-workers] gzip and tcpdump
Tcpdump timestamp
Man page of TCPDUMP, You can use the -tttt option: $ tcpdump -tttt -nr tmp.pcap reading from file tmp.pcap, link-type EN10MB (Ethernet) 2018-01-19 17:50:43.275918 Tcpdump prints out a description of the contents of packets on a network interface that match the Boolean expression; the description is preceded by a time stamp, printed, by default, as hours, minutes, seconds, and fractions of a second since midnight.
TcpDump: showing the absolute timestamp (date + time) of pcap file , -tttt : Give maximally human-readable timestamp output. -X : Show the packet's contents in both hex and ASCII. -XX : Same as -X, but also shows I have written a linux script to dump the packets using tcpdump command to a file dcn.pcap to max limit of 20MB. Is there anyway to add the timestamp to the filename ? The time stamp from the beginning of the file like 2014_date_time.pcap. tcpdump -w dcn.pcap -C 20 -i eth0 -s 65535 dst net 244.11.11
TCPDUMP: a simple cheatsheet, Tcpdump is a command line utility that allows you to capture and analyze The first field, 08:41:13.729687, represents the timestamp of the Time stamp provided by the host on which the capture is being done. This is a high-precision time stamp, synchronized with the host operating system's clock. It might be more expensive to fetch than PCAP_TSTAMP_HOST_LOWPREC. PCAP_TSTAMP_HOST_HIPREC_UNSYNCED - host_hiprec_unsynced Time stamp provided by the host on which the capture is being done.
Editcap change ip address
Change IP address in packet capture file (faking IP), I'm sure you bumped into situations where you needed to fake IP address in a capture file. This maybe required when you're trying to send the Change your IP Address using the Best VPN. Find a VPN to Change your IP Address!
Modify ip addresses in a socks capture pcap, TL;DR. The --endpoints option of tcprewrite is what you're looking for. It requires a cachefile from tcpprep : $ tcpprep --port --pcap=in.pcap --cachefile=in.cache Change Your IP Using a Secure VPN. Encrypt Your Internet Connection & Surf the Web Privately & Securely!
D.7. editcap: Edit capture files, editcap is a general-purpose utility for modifying capture files. A value of -0 will set all packets to the timestamp of the first packet. Useful to remove duplicated packets taken on several routers (different mac addresses for example). e.g. -I 26 in case of Ether/IP will ignore ether(14) and IP header(20 - 4(src ip) - 4(dst ip)). Change a Router's IP Address . To change the router's IP address, log in to the router as an administrator. From the control panel, change the IP address to whatever you like. However, this IP address is usually changed when there's a problem with it. The default IP address should suffice for most situations.
Tcpdump to file
Tshark Cheat Sheet
D.3. tcpdump: Capturing with 'tcpdump' for viewing with Wireshark, Older versions of tcpdump truncate packets to 68 or 96 bytes. If this is the case, use -s to capture full-sized packets: $ tcpdump -i -s 65535 -w . tcpdump man page. When you create a pcap file using tcpdump it will truncate your capture file to shorten it and you may not able to understand that. I am writing this post, so that you can create a pcap file effectively. You can use following command to capture the dump in a file: tcpdump -s 0 port ftp or ssh -i eth0 -w mycap.pcap. In above

extcap - The extcap interface
idl2wrs - CORBA IDL to Wireshark Plugin Generator
mergecap - Merges two or more capture files into one
mmdbresolve - Read IPv4 and IPv6 addresses and print their IP geolocation information.
randpkt - Random packet generator
randpktdump - Provide an interface to generate random captures using randpkt
rawshark - Dump and analyze raw pcap data
reordercap - Reorder input file by timestamp into output file
sshdump - Provide interfaces to capture from a remote host through SSH using a remote capture binary.
text2pcap - Generate a capture file from an ASCII hexdump of packets
tshark - Dump and analyze network traffic
udpdump - Provide an UDP receiver that gets packets from network devices (like Aruba routers) and exports them in PCAP format.
wireshark-filter - Wireshark display filter syntax and reference
wireshark - Interactively dump and analyze network traffic
Capture filtering is handled by libpcap, and its documentation is part of the libpcap distribution.
I have a lot of traffic...
ANSWER: SteelCentral™ AppResponse 11
- • Full stack analysis – from packets to pages
- • Rich performance metrics & pre-defined insights for fast problem identification/resolution
- • Modular, flexible solution for deeply-analyzing network & application performance
Editcap split pcap
Splitting pcap files in wireshark, Up vote 21 Down vote. Use the editcap utility which is distributed with Wireshark. I found a great tool for splitting pcap files: PcapSplitter. It's part of the Editcap is a program that reads some or all of the captured packets from the infile, optionally converts them in various ways and writes the resulting packets to the capture outfile (or outfiles). By default, it reads all packets from the infile and writes them to the outfile in pcap file format.
how to split a pcap file into a set of smaller ones, Splitting a big capture file. If you have a big file you can quite easily split it into smaller files,using editcap. editcap is a command line tool that is I know this answer is a little late, but it may serve other people as well. I found a great tool for splitting pcap files: PcapSplitter.It's part of the PcapPlusPlus library which means it's cross-platform (Win32, Linux and Mac OS), and it can split pcap files based on different criteria such as file size (what you seem to need) but also by connection, client/server IP, server port (similar to
PCAP Split and Merge | Packet-Foo, Editcap is a program that reads some or all of the captured packets from the infile, optionally Editcap is able to detect, read and write the same capture files that are pcap(3), wireshark(1), tshark(1), mergecap(1), dumpcap(1), capinfos(1), If you have a big file you can quite easily split it into smaller files,using editcap. editcap is a command line tool that is installed together with Wireshark. This is why it is a good idea to add the Wireshark installation path to your path variable so that you can run the command line tools everywhere.
Tshark
tshark, TShark is a network protocol analyzer. It lets you capture packet data from a live network, or read packets from a previously saved capture file, either printing a Installation is a gateway drug. Different systems will report different interfaces. tshark will treat the first interface as the default interface and capture from it by default.
D.2. tshark: Terminal-based Wireshark, TShark is a terminal oriented version of Wireshark designed for capturing and displaying packets when an interactive user interface isn't necessary or available. Wireshark is the world's foremost and widely-used network protocol analyzer. It lets you see what's happening on your network at a microscopic level and is the de facto (and often de jure) standard across many commercial and non-profit enterprises, government agencies, and educational institutions.
tshark(1): Dump/analyze network traffic, TShark is a network protocol analyzer. It lets you capture packet data from a live network, or read packets from a previously saved capture file, either Tshark.dev. tshark.dev is your complete guide to working with packet captures on the command-line. The focus is on doing everything in the CLI because that is an interface your scripts and programs can use. Bash features prominently here, with some examples also in python and ruby.
Tcpdump cheat sheet
tcpdump Cheat Sheet - Complete With Full Examples, The tcpdump cheat sheet covers: Installation commands; Packet capturing options; Logical operators; Display/Output options; Protocols; Common tcpdump Cheat Sheet A commonly used and priceless piece of software, tpcdump is a packet analyzer that packs a lot of punch for a free tool. We put together a list of essential commands and put them in the tcpdump cheat sheet to help you get the most out of it.
[PDF] tcpdump, Command Line Options. -A. Print frame payload in ASCII. -c Exit after capturing count packets. -D. List available interfaces. -e. Print link-level headers. tcpdump Cheat Sheet Installation Commands CENT OS and REDHAT $ sudo yum install tcpdump Fedora $ dnf install tcpdump Ubuntu, Debian and Linux Mint #apt-get install tcpdump
TCPDUMP: a simple cheatsheet, tcpdumpruns under the command line and allows the user to display TCP/IP and other packets being transmitted or received over a network to tcpdump usage tcpdump [-aAenStvxX] [-F filterfile] [-i int] [-c n] [-r pcapfile] [-s snaplen] [-w pcapfile] [‘bpf filter'] -A display payload -c n display first n packets-D list interfaces -e display data link header -F read filter expression from file -i listen on specified interface -n do not resolve IP addresses / ports
Tcpdump count packets
tcpdump, I wouldn't use tcpdump (or tshark ) for this. Instead I'd use iptables to count the packets over a period of time # Prepare two sets of counters and -c count Exit after receiving count packets. --count Print only on stderr the packet count when reading capture file(s) instead of parsing/printing the packets. If a filter is specified on the command line, tcpdump counts only packets that were matched by the filter expression. -C file_size
Man page of TCPDUMP, There is, in fact, no packet count in the file header (because the format was designed to be writable in tcpdump -r test.cap 2>/dev/null| wc -l. Packets 'received by filter.' The meaning of this depends on the OS on which you're running tcpdump, and possibly on the way the OS was configured.If a filter was specified on the command line, on some OSs it counts packets regardless of whether they were matched by the filter expression, and on others it counts only packets that were matched by the filter expression and were processed by tcpdump.
Tcpdump - counting outgoing and incoming UDP packets, Know your network with this powerful packet capture tool. Another tip is to use count -c on the remote tcpdump to allow the capture to finish I am interested in getting a count of all LDAP/Kerberos/DNS packets. I tried the following, but this captures the full packet. tcpdump -i any -Z root 'tcp port 389 or tcp port 88 or udp port 53' -w ~/ldap_kerberos_dns.cap . Is there a way I can just capture how many ldap/Kerberos/DNS packets were exchanged without actually capturing the full
Tcpdump gzip
Write tcpdump output to compressed / gziped file, avoid trying to run tcpdump if gzip obviously failed to start { [ -n '$gzip_pid' ] && [ '$gzip_pid' -gt 0 ] && kill -0 '$gzip_pid'; } || exit 1 tcpdump For example, specifying -z gzip or -z bzip2 will compress each savefile using gzip or bzip2. Note that tcpdump will run the command in parallel to the capture, using the lowest priority so that this doesn't disturb the capture process.
Man page of TCPDUMP, tcpdump -w - | ( gzip -c > output.pcap.gz & ). The other is to just have the files written out in their normal format, and then use a post-processing For this I start using following tcpdump command and capture them to a file: tcpdump -n -i eth0 dst port 53 >> dns_data.log But the file size is high when I run this for long time. How can I capture this to a compress file? I tried below command but its not working. tcpdump -n -i eth0 dst port 53 | bzip2 -c >> dns_data.bz2
I/O Efficient GZip Compression of Packet Captures, tcpdump -i eth0 -w - | ssh forge.remotehost.com -c arcfour,blowfish-cbc -C -p 50005 'cat - | gzip > /tmp/eth0.pcap.gz' - (TCPDUMP & Save -----Original Message----- From: owner-tcpdump-workers sandelman ottawa on ca [mailto:owner-tcpdump-workers sandelman ottawa on ca]On Behalf Of Rob Braun Sent: Wednesday, February 26, 2003 02:16 To: Guy Harris Cc: tcpdump-workers tcpdump org Subject: Re: [tcpdump-workers] gzip and tcpdump
Tcpdump timestamp
Man page of TCPDUMP, You can use the -tttt option: $ tcpdump -tttt -nr tmp.pcap reading from file tmp.pcap, link-type EN10MB (Ethernet) 2018-01-19 17:50:43.275918 Tcpdump prints out a description of the contents of packets on a network interface that match the Boolean expression; the description is preceded by a time stamp, printed, by default, as hours, minutes, seconds, and fractions of a second since midnight.
TcpDump: showing the absolute timestamp (date + time) of pcap file , -tttt : Give maximally human-readable timestamp output. -X : Show the packet's contents in both hex and ASCII. -XX : Same as -X, but also shows I have written a linux script to dump the packets using tcpdump command to a file dcn.pcap to max limit of 20MB. Is there anyway to add the timestamp to the filename ? The time stamp from the beginning of the file like 2014_date_time.pcap. tcpdump -w dcn.pcap -C 20 -i eth0 -s 65535 dst net 244.11.11
TCPDUMP: a simple cheatsheet, Tcpdump is a command line utility that allows you to capture and analyze The first field, 08:41:13.729687, represents the timestamp of the Time stamp provided by the host on which the capture is being done. This is a high-precision time stamp, synchronized with the host operating system's clock. It might be more expensive to fetch than PCAP_TSTAMP_HOST_LOWPREC. PCAP_TSTAMP_HOST_HIPREC_UNSYNCED - host_hiprec_unsynced Time stamp provided by the host on which the capture is being done.
Editcap change ip address
Change IP address in packet capture file (faking IP), I'm sure you bumped into situations where you needed to fake IP address in a capture file. This maybe required when you're trying to send the Change your IP Address using the Best VPN. Find a VPN to Change your IP Address!
Modify ip addresses in a socks capture pcap, TL;DR. The --endpoints option of tcprewrite is what you're looking for. It requires a cachefile from tcpprep : $ tcpprep --port --pcap=in.pcap --cachefile=in.cache Change Your IP Using a Secure VPN. Encrypt Your Internet Connection & Surf the Web Privately & Securely!
D.7. editcap: Edit capture files, editcap is a general-purpose utility for modifying capture files. A value of -0 will set all packets to the timestamp of the first packet. Useful to remove duplicated packets taken on several routers (different mac addresses for example). e.g. -I 26 in case of Ether/IP will ignore ether(14) and IP header(20 - 4(src ip) - 4(dst ip)). Change a Router's IP Address . To change the router's IP address, log in to the router as an administrator. From the control panel, change the IP address to whatever you like. However, this IP address is usually changed when there's a problem with it. The default IP address should suffice for most situations.
Tcpdump to file
Tshark Cheat Sheet
D.3. tcpdump: Capturing with 'tcpdump' for viewing with Wireshark, Older versions of tcpdump truncate packets to 68 or 96 bytes. If this is the case, use -s to capture full-sized packets: $ tcpdump -i -s 65535 -w . tcpdump man page. When you create a pcap file using tcpdump it will truncate your capture file to shorten it and you may not able to understand that. I am writing this post, so that you can create a pcap file effectively. You can use following command to capture the dump in a file: tcpdump -s 0 port ftp or ssh -i eth0 -w mycap.pcap. In above
Tshark Tutorial
An introduction to using tcpdump at the Linux command line , Tcpdump is a command line utility that allows you to capture and Tcpdump creates a file in binary format so you cannot simply open it with a tcpdump port 80-w capture_file. You can read PCAP files by using the -r switch. Note that you can use all the regular commands within tcpdump while reading in a file; you're only limited by the fact that you can't capture and process what doesn't exist in the file already. tcpdump-r capture_file. Advanced
Tshark Cheat Sheet Download
Use tcpdump to capture in a pcap file (wireshark dump), tcpdump is a command line network sniffer, used to capture network packets. · -s 0 will set the capture byte to its maximum i.e. 65535, after this Older versions of tcpdump truncate packets to 68 or 96 bytes. If this is the case, use -s to capture full-sized packets: $ tcpdump -i -s 65535 -w You will have to specify the correct interface and the name of a file to save into. In addition, you will have to terminate the capture with ^C when you believe you have captured